Tech
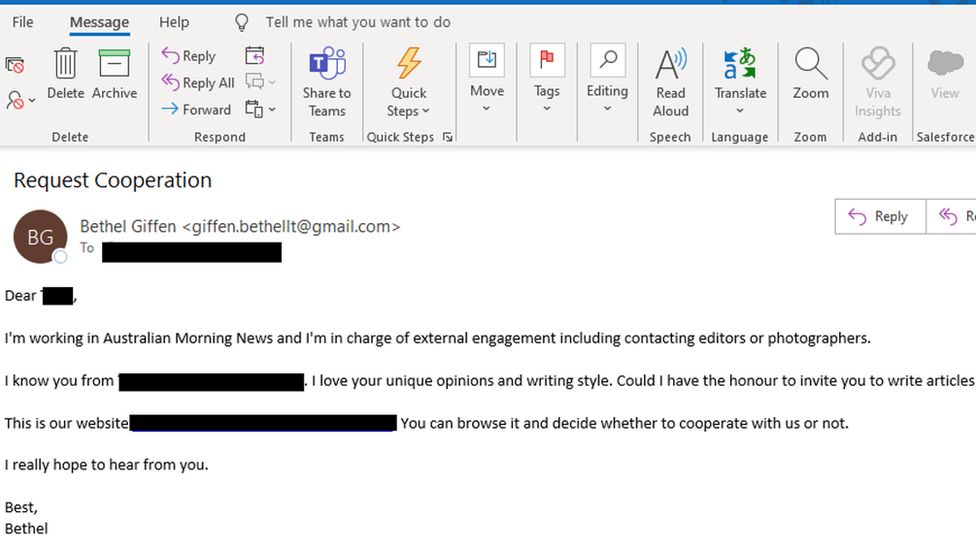
Hackers target politicians with fake news webs
-

 Fashion2 years ago
Fashion2 years agoFive wedding outfits for just £29!
-

 Politics2 years ago
Politics2 years agoMikhail Gorbachev changed history
-
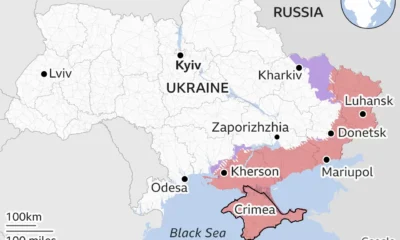
 Politics2 years ago
Politics2 years agoTracking the war with Russia
-

 Everything About Youtube2 years ago
Everything About Youtube2 years agoThe Twitter Artist who makes a Fortune off YouTube Thumbnails while Studying.
-

 Fashion2 years ago
Fashion2 years agoOn presents first ever shoe made from carbon
-

 Politics2 years ago
Politics2 years agoCharles is announced to be the new King
-

 Tech2 years ago
Tech2 years agoThe rise of the AI artists stirs debate
-

 Everything About Youtube2 years ago
Everything About Youtube2 years agoEveryone knows YouTube, but not how it works.