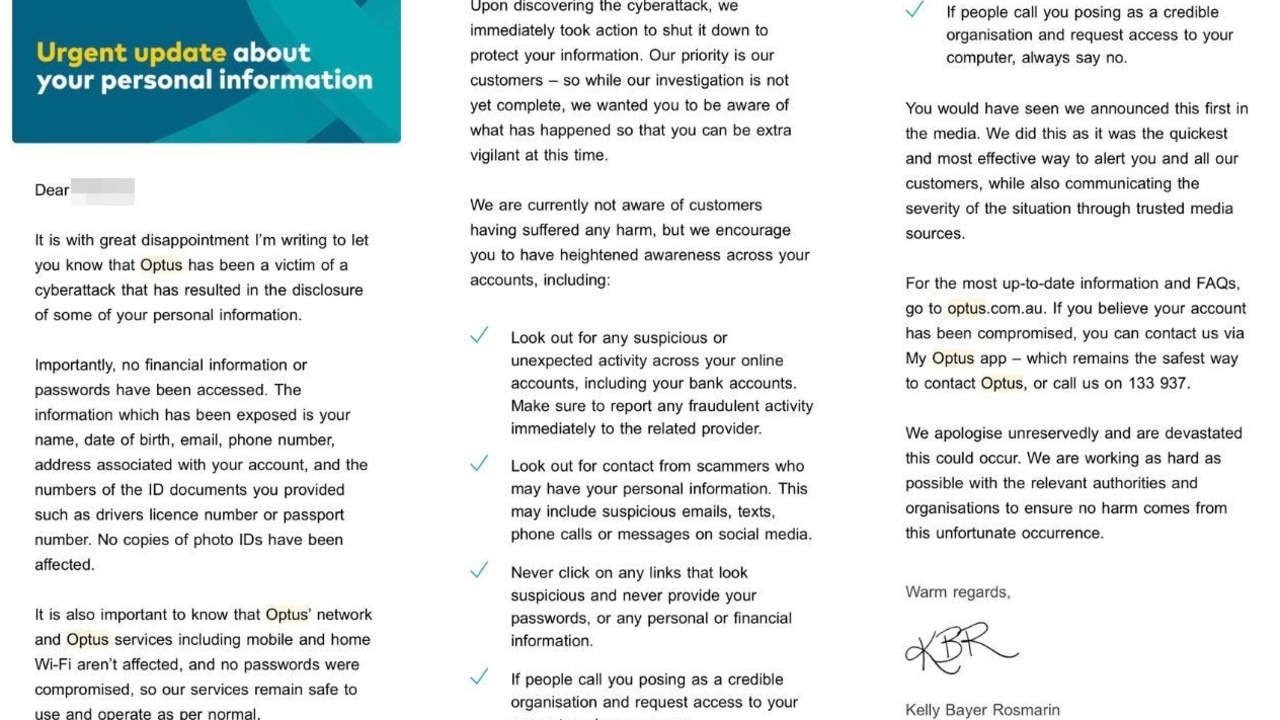
Millions of Australians may have had their personal information stolen and sold by the cybercriminals behind this week’s massive attack against Optus.
People’s names, dates of birth, phone numbers, and email addresses have been exposed, Optus has confirmed.
Some current and former customers have even had their passport or driver’s licence numbers compromised.
The people worst affected are likely to hear from Optus first, the telco’s chief executive said on Friday.
“Our priority is going to start with the customers where the most fields may have been exposed,” Kelly Bayer-Rosmarin said.
“So over the next few days, all customers will know in what category they fall. And we’re hoping for most of them that this does not put them in harm’s way.”
Ms Bayer-Rosmarin did not specify the number of Optus customers affected by the data breach, but the company believes it’s “considerably less” than the “worst case scenario” of 9.8m customers.
Cyber experts fear some people will be alerted to the data theft by criminals online instead of Optus.
“The first sign would be getting a flurry of phishing emails,” cybersecurity expert and StickmanCyber founder Ajay Unni told NCA NewsWire.
“There could be calls, emails or text messages.”
Typically fraudsters try to use personal data to gain access to people‘s accounts or devices, Mr Unni said.
Scammers have even been known to use information about people’s home addresses to send them letters in the mail.
Depending on the amount of data leaked about each customer, scammers could have enough information to take over bank accounts, or open new, fraudulent ones in the names of victims.
Mr Unni recommended that people use two-factor identification for their online accounts, meaning an extra layer of protection on top of the password.
A common way to do that is to require a code to be sent via SMS before an account can be accessed.
Using different passwords for different services is another way to stay safe.
Mr Unni also recommended never clicking on a link in a suspicious email.
He said that if a customer receives an email from Optus and are wondering if it’s legitimate, they should contact the company themselves, rather than clicking on any links in that email.
The federal government‘s Australian Cyber Security Centre recommended customers who worry they’ve been compromised use the web application “Have you been hacked?”
Another good resource is the site “HaveIbeenpwned.com”, which will track whether your personal information has been included in a data dump.
Optus currently has more than 5.8 million active users, but previous customers from as far back as 2017 could see their data stolen in the cyber attack. Close to 10 million people are believed to have been affected.
The telco said it was “currently not aware of customers having suffered any harm”, but reassured customers it was working as hard as possible with relevant authorities to ensure no harm would eventuate.
Ms Bayer-Rosmarin said on Thursday that Optus were engaging with IDcare, a not-for-profit national identity and cyber security support service. However, given the enormous scale of the breach, the service may be unable to provide case-by-case assistance to customers.
News of the breach broke on Thursday, during the National Day of Mourning for the passing of Queen Elizabeth II. Optus chose to disseminate the breaking news through the media, instead of utilising their phone network (which it said remained uncompromised) or social media.
In an email to affected customers, the Optus CEO said she was “devastated” that the telco had been “the victim of a cyberattack”. Customers who had their information stolen were urged to be “extra vigilant” and “have heightened awareness across your accounts”.
Investigations into the matter are ongoing and will involve the Australian Federal Police, according to Optus.
Customers who believe their data may have been compromised, or who have specific concerns, were asked to contact Optus through the My Optus App (the company said this is the safest way to interact with Optus), or by calling 133 937.
Reports / Trainviral /

 Fashion2 years ago
Fashion2 years ago
 Politics2 years ago
Politics2 years ago
 Politics2 years ago
Politics2 years ago
 Everything About Youtube2 years ago
Everything About Youtube2 years ago
 Fashion2 years ago
Fashion2 years ago
 Politics2 years ago
Politics2 years ago
 Tech2 years ago
Tech2 years ago
 Everything About Youtube2 years ago
Everything About Youtube2 years ago